
The Best Backup Strategies to Protect Your Files from Data Loss
Introduction
Data loss is an ever-present risk in today's digital world—whether it stems from hardware failure, malware, accidental deletion, or even natural disasters. Because our personal and professional lives rely so heavily on digital files, losing access to important documents, cherished photos, or critical business information can be devastating. A robust backup strategy is your best defense against these worst-case scenarios, ensuring that even if your main copy is compromised, you have a fallback that preserves your essential data.
In this comprehensive guide, we'll explore various backup strategies to help you effectively safeguard your files. From understanding fundamental concepts like the 3-2-1 approach to selecting the right media—cloud storage, external drives, network-attached solutions—and implementing automation, encryption, and versioning, you'll learn how to protect your data from loss. By the end, you'll be prepared to design a backup system that fits your needs, whether you're a casual home user or an enterprise environment responsible for large-scale data.
1. Why Backups Matter
-
Hardware Failures: Hard drives and SSDs can fail unexpectedly, leaving important data inaccessible.
-
Human Error: Accidental deletions or overwrites can wipe out hours of work.
-
Malware / Ransomware: Files can be corrupted or encrypted, forcing you to pay a ransom (with no guarantee of success).
-
Theft or Loss: Laptops or external drives might be stolen or misplaced, taking your data with them.
-
Natural Disasters: Fires, floods, or power surges can destroy devices.
Scenario: A freelance photographer’s main drive fails one day, losing a half-completed wedding project. Thanks to a nightly backup, she restores the entire session, preserving her reputation and client trust.
2. Core Backup Principles
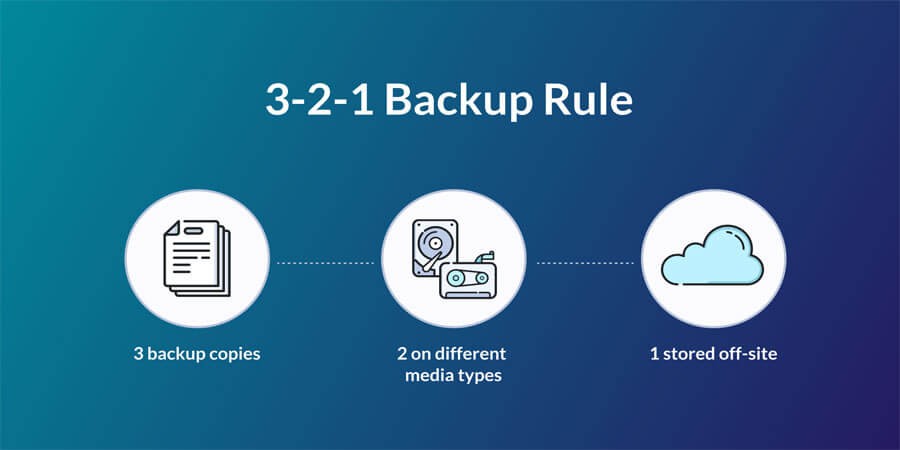
2.1 The 3-2-1 Rule
-
3 copies: Keep at least three copies of your data (the original + two backups).
-
2 different media: Store them on two different media (e.g., local external HDD + cloud backup). This guards against a single point of failure.
-
1 offsite: Keep one copy offsite (physically removed from your primary location) to protect against local disasters.
2.2 Versioning
-
Ensures older file versions remain available. If you accidentally overwrite or corrupt a file, you can revert to an earlier iteration.
-
Cloud services or backup software that supports version histories help mitigate “Oops, I saved the wrong version!” moments.
2.3 Automation
-
Manual backups are prone to being forgotten. A scheduled or real-time system ensures consistency and reduces human error.
Advice: By designing a strategy around these fundamentals, you drastically minimize catastrophic data loss.
3. Types of Backup Approaches
3.1 Full Backup
-
Copies all files and folders every time.
-
Pros: Straightforward, quick restoration (just the one set needed).
-
Cons: Requires large space, slower if you have massive data sets.
3.2 Incremental Backup
-
After a full backup, only files changed since the last incremental are saved.
-
Pros: Faster, smaller backups once the initial full is done.
-
Cons: To restore, you need the full backup + all subsequent incremental sets.
3.3 Differential Backup
-
After a full backup, each differential captures changes since the last full. More data than incrementals, but faster to restore.
Scenario: A small business runs a full backup on Sunday, then daily incrementals. If Monday’s data gets corrupted on Tuesday, they restore the Sunday full plus Monday’s incremental, limiting lost changes.
4. Choosing Your Backup Media
4.1 External Hard Drives
-
Pros: Cost-effective, portable, easy for offline backups.
-
Cons: Vulnerable to local disasters, theft, mechanical failure.
-
Best For: Single-machine or small-scale usage, quick manual or scheduled backups.
4.2 Network Attached Storage (NAS)
-
Pros: Central storage for multiple machines, RAID redundancy, can integrate with cloud sync.
-
Cons: Upfront cost, some configuration complexity.
-
Ideal: Households or small offices wanting a local “private cloud.”
4.3 Cloud Storage / Backup
-
Pros: Offsite by default, easy for continuous or versioned backups, accessible from anywhere.
-
Cons: Monthly/annual fees, reliant on stable internet, potential provider trust or lock-in.
-
Examples: Backblaze, IDrive, CrashPlan, or general cloud (Dropbox/Google Drive/OneDrive) with backup features.
4.4 Tape Storage (LTO)
-
Pros: Long shelf life, cost-effective for large enterprise archives.
-
Cons: Slower access, specialized hardware, typical for corporate or institutional setups.
Pro Tip: Combining local external drives + a cloud solution often yields the best mix of speed, cost, and offsite protection.
5. Implementing the 3-2-1 Rule
5.1 Example Setup
-
3 copies: Original data on your main computer, a local external HDD backup, plus an encrypted cloud backup.
-
2 media: HDD for local copy, cloud (SaaS or IaaS) for offsite.
-
1 offsite: The cloud portion covers geographical separation.
5.2 Variation
-
For those dealing with huge data volumes or extremely sensitive data, a second local backup could be on a NAS. Or store a physically separate disk at a friend’s house.
Scenario: A wedding photographer keeps the main library on a local SSD, duplicates nightly to a RAID NAS at home, and uses Backblaze for continuous offsite coverage.
6. Automating Your Backups
6.1 Built-In OS Tools
-
Windows: File History (for user data) + system image backup. Schedules can be set daily or more frequently.
-
macOS: Time Machine does hourly incremental backups, user-friendly restore timeline.
-
Linux: Tools like Deja Dup, Timeshift, or custom scripts.
6.2 Third-Party Software
-
Acronis Cyber Protect Home Office: Full system images + cloud backups.
-
EaseUS Todo Backup: Wizard-based for scheduling, cloning, imaging.
-
Macrium Reflect: Reliable disk cloning, scheduling in Windows.
6.3 Cloud Backup Services
-
Backblaze: Unlimited personal backup for one PC, easy set-and-forget. Backs up all user data.
-
IDrive: Cross-platform, can handle multiple devices, includes file sync.
-
Carbonite: Targets small business or personal usage with continuous backups.
Pro Tip: Setting an automated schedule (e.g., daily incremental, weekly full) ensures coverage for frequent changes without constant manual intervention.
7. Encryption and Security
7.1 Encrypting Backup Data
-
Prevents unauthorized eyes from seeing your files if the drive or cloud is compromised.
-
Tools like BitLocker (Windows), FileVault (macOS), VeraCrypt containers, or encryption features built into backup apps.
7.2 Zero-Knowledge Cloud
-
Providers (Sync.com, Tresorit, SpiderOak) never see your unencrypted data. Or use client-side encryption (Duplicati, Cryptomator) before upload.
7.3 MFA & Passwords
-
For cloud backup accounts, use multi-factor authentication. Keep strong passphrases for encryption keys.
Scenario: A small business worried about client confidentiality picks IDrive with a private encryption key set on the client side. Even IDrive staff can’t decrypt it.
8. Versioning & Retention Policies
-
Incremental Versioning: Cloud solutions or local backup software store older copies. If you accidentally overwrite a crucial doc, you can revert.
-
Retention Durations: Decide how long older versions remain. Some keep 30 days, others indefinite.
-
Storage Space: The longer you keep older versions, the more space you consume.
Advice: For personal usage, a month’s worth of versions might suffice. Businesses might need months or years for compliance or archival reasons.
9. Backup Frequency and Strategies
9.1 Continuous vs. Scheduled
-
Continuous/Real-Time: E.g., Time Machine’s hourly increments or Cloud backup scanning for new files. Minimizes potential data loss but uses more system resources.
-
Scheduled: Daily or weekly backups for stable data sets or large volumes. Less overhead.
9.2 Full + Differential vs. Full + Incremental
-
Differential is simpler to restore (only the full + the last differential). Incremental is more space-efficient but requires chaining multiple sets.
Scenario: A developer doing daily code changes sets up a nightly incremental backup plus a weekly full. Also uses real-time version control (Git) for the code itself.
10. Offsite Storage Methods
10.1 Physical Offsite
-
Periodically rotate external drives to a different location (a friend’s house, safe deposit box, or second office). Minimizes local disaster risk.
-
Keep them encrypted if you’re storing them outside.
10.2 Cloud / Internet
-
Automatic and continuous for remote coverage. If your local environment is destroyed, the data remains.
-
Must trust the provider or encrypt on your side.
10.3 Hybrid
-
Local backups for quick restoration + cloud/offsite for disaster scenarios. The standard approach for robust coverage.
Pro Tip: Evaluate your risk tolerance. If local floods or fires are possible, a purely local approach is insufficient.
11. Testing Your Restores
11.1 Importance of Recovery Drills
-
A backup is only valuable if you can actually restore from it. Overlooked corruption or misconfig can ruin your plan.
11.2 Partial or Full Test
-
Try restoring a few random files or do a complete system restore in a test environment. Verifies data integrity.
11.3 Frequency
-
Corporate best practice might schedule monthly or quarterly test restores. Personal usage might do a check every few months.
Scenario: A small design agency does a random restore test each quarter, picking a random project folder from the backup to confirm it’s valid and complete.
12. Enterprise Backup Solutions
12.1 Managed Backup Services
-
Tools like Veeam, Commvault, or Acronis for server and VM backups. Offer scheduling, deduplication, encryption, dashboards.
12.2 Backup Appliances
-
Hardware-based solutions that replicate data from multiple servers, storing incremental snapshots. Can replicate to an offsite data center.
12.3 Virtual Machine Snapshots
-
Quick revert if a VM is corrupted or a patch goes wrong.
Outcome: Larger organizations rely on advanced solutions that unify backups across multiple servers, databases, apps, and remote sites.
13. Handling Large or Constantly Changing Data
13.1 Incremental Forever
-
Some solutions do one full backup initially, then only incrementals forever, merging older increments in the background.
-
Minimizes repeated full backups for huge data sets.
13.2 Deduplication
-
Identical blocks across backups are stored once, drastically cutting storage usage for repeated data sets (like multiple OS images).
13.3 Snapshots
-
Filesystem-level snapshots (ZFS, Btrfs, Windows Volume Shadow Copy) can freeze a consistent view of the data for backup, avoiding partial file states.
Scenario: A data analytics firm uses a deduplicating backup system for daily backups of large logs, saving 70% space by ignoring repeated blocks.
14. Specialized Backup Considerations
14.1 Database Backups
-
Traditional file copying might produce inconsistent or partial DB states if it’s actively in use. Instead use DB-specific dump or replication.
14.2 Email Servers
-
For Exchange or IMAP-based systems, using mailbox-level or server-level backups. Possibly exporting PST or EML for local copies.
14.3 Cloud Apps
-
SaaS solutions like Office 365 or Google Workspace also need backups. Third-party tools can regularly extract data from them.
Pro Tip: A single universal file-based approach might not suffice for complex applications. Use recommended backup methods from the vendor.
15. Considering Security in Backups
15.1 Encryption in Transit & At Rest
-
Tools that handle SSL or secure protocols for remote backups. On local media, encrypt volumes or container.
15.2 Ransomware-Resistant
-
Keep at least one offline or immutable backup set.
-
Some solutions lock backups from modification after creation.
15.3 Access Permissions
-
Ensure backup destinations aren’t publicly accessible or easily modifiable by normal users, preventing sabotage.
Scenario: An enterprise keeps a WORM (Write Once Read Many) storage for monthly archives, unaffected by future editing or encryption attempts.
16. Minimizing Impact on Performance
16.1 Scheduling Off-Hours
-
Large backups can hog CPU, disk, or network resources. Plan them for night or weekends if real-time backups aren’t necessary.
16.2 Incremental / Differential
-
Fewer resources than daily full backups, especially if your data changes partially.
16.3 Throttling
-
Some backup software can limit bandwidth usage or CPU load, preventing slowdown of day-to-day tasks.
Pro Tip: A balanced approach ensures backups happen frequently enough but don’t degrade productivity.
17. Common Mistakes to Avoid
-
No Offsite Copy: A single external drive in the same building means one fire or theft can destroy all copies.
-
Never Testing Restores: Backups might be silently failing or corrupt. You only discover it in a crisis.
-
Keeping Only One Version: Overwrites or partial corruption remain unstoppable if you can’t revert.
-
Unsecured Backups: Not encrypting or protecting the backup storage leaves data exposed if backups are lost or stolen.
-
Relying on RAID: RAID is not a backup; it only guards against disk hardware failure, not user error or malware.
Advice: A carefully planned and tested backup system addresses each of these pitfalls, guaranteeing true data safety.
18. Conclusion
The best backup strategies revolve around fundamental guidelines: multiple copies (3-2-1 rule), robust automation, encryption for data security, offsite storage to tackle disasters, and thorough restore testing. By mixing local backups for quick recovery with a reliable cloud or offsite solution for catastrophic scenarios, you’ll ensure your files remain safe from hardware crashes, malware incidents, and human mistakes.
With versioning in place, you can roll back undesired changes or retrieve older edits, while advanced features like deduplication, snapshotting, or incremental scheduling keep overhead reasonable. Whether you’re a personal user guarding family photos, a small business protecting customer data, or an enterprise managing mission-critical systems, systematically applying these strategies defends against the heartbreak and downtime of data loss.
In essence, backups are your last line of defense. When all else fails—hardware, OS, antivirus—the presence of a well-maintained backup stands between you and irreparable disaster. By building and refining a multi-layered approach now, you safeguard peace of mind, productivity, and the trust placed in your digital environment.
Popular articles




Comments (0)